Digital threats are increasingly sophisticated and pervasive, and the need for robust cybersecurity measures has never been more critical. Among the diverse range of tools available to IT professionals, Endpoint Detection and Response (EDR) solutions have emerged as a vital component in the fight against cyber threats.
Brief Overview of Endpoint Detection and Response (EDR) Solutions
Endpoint Detection and Response (EDR) solutions are advanced cybersecurity tools designed to monitor, detect, and respond to potential threats on endpoint devices. These devices, which include laptops, smartphones, tablets, and servers, are often the primary targets for cybercriminals. EDR security solutions provide continuous surveillance of these devices, identifying and mitigating threats in real-time, thereby fortifying the organization's digital defenses.
Endpoint security solutions leverage advanced technologies such as machine learning and behavioral analytics to identify anomalous activities that could signify a cyber threat. Once a potential threat is detected, EDR solutions can respond automatically, isolating the affected device and mitigating the threat to prevent further damage.
Importance of EDR products in Today's Digital Landscape
With the increase of remote work and the Internet of Things (IoT), endpoint devices have skyrocketed, expanding the potential attack surface for cybercriminals. This makes the role of EDR solutions more crucial than ever.
EDR solutions provide comprehensive visibility into an organization's network, enabling IT professionals to monitor all endpoint devices continuously. This level of visibility is crucial in detecting and responding to threats promptly, reducing the potential impact on the organization.
Moreover, EDR solutions are not just reactive but also proactive. They can identify vulnerabilities and potential threats before they become active attacks, allowing organizations to fortify their defenses and prevent breaches.
In the face of evolving cyber threats, EDR solutions are essential in maintaining robust cybersecurity. Organizations can safeguard their digital assets effectively by providing real-time threat detection and response, ensuring business continuity, and protecting their reputation.
Stay tuned as we delve deeper into the top 5 Endpoint Detection and Response solutions, providing the insights you need to choose the right EDR solution for your organization.
Top 5 Endpoint Detection and Response Solutions
As we delve into Endpoint Detection and Response solutions, we must note that not all EDR solutions are created equal. Different providers offer unique features and capabilities, making some solutions better suited to certain organizations. In this section, we'll explore the top 5 EDR solutions with a deep dive into ESET PROTECT Enterprise.
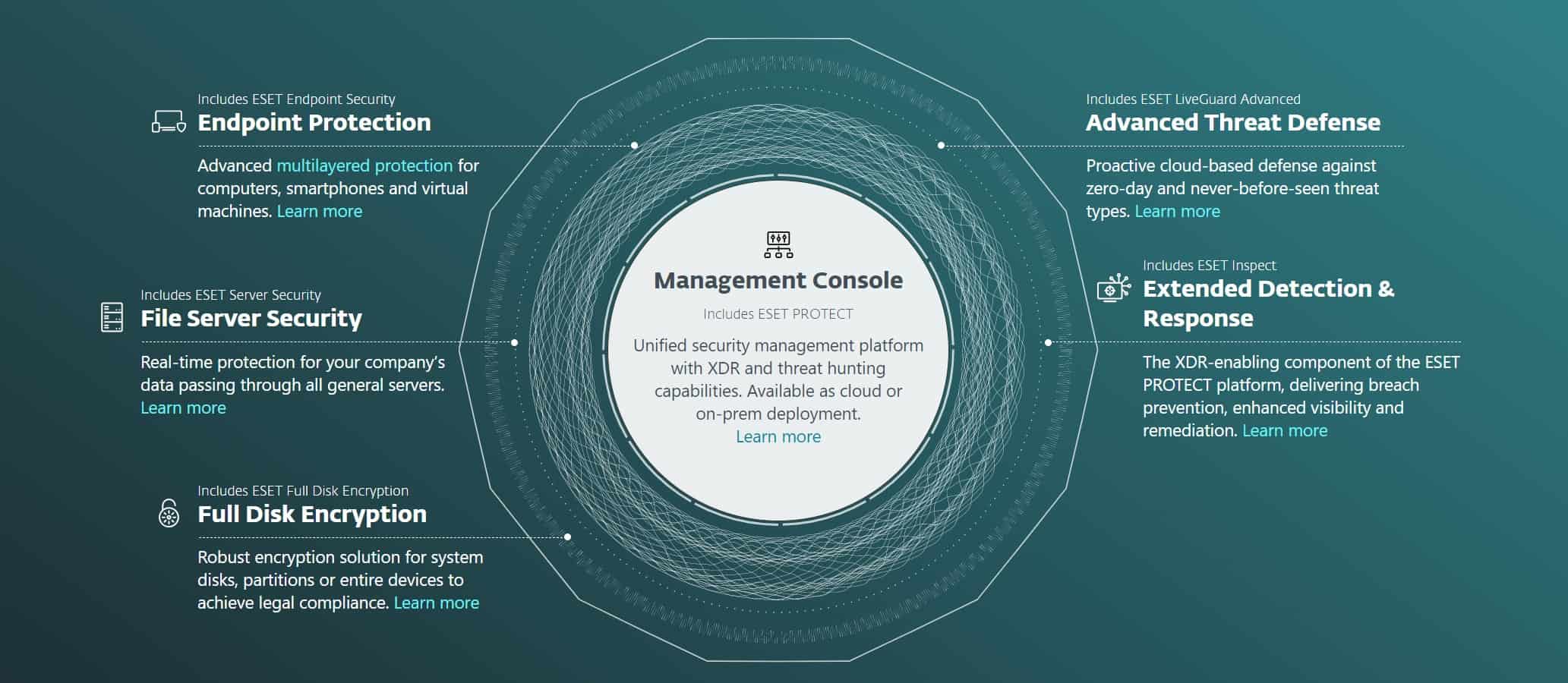
ESET PROTECT Enterprise
Overview of ESET as a Provider
ESET has been a global cybersecurity company at the forefront of digital protection for over 30 years. Renowned for its pioneering work in heuristic detection, ESET has consistently been recognized for its innovation and high-quality solutions. With a presence in over 200 countries and territories, ESET provides comprehensive cybersecurity solutions for businesses of all sizes.
Key Features of ESET PROTECT Enterprise
ESET PROTECT Enterprise is a comprehensive EDR solution that offers a range of features designed to provide robust protection for endpoint devices. These include:
- Multilayered Technology: ESET PROTECT Enterprise uses multilayered technology to detect and respond to threats at different stages of the attack process, providing comprehensive protection.
- Cloud-Based Management: The solution offers a cloud-based management console, allowing IT teams to monitor and manage security from anywhere.
- Advanced Machine Learning: ESET's advanced machine learning models are trained on a vast array of safe and malicious samples, enabling them to identify and respond to threats accurately.
- Full Disk Encryption: ESET PROTECT Enterprise offers full disk encryption, ensuring that data remains secure even if a device is lost or stolen.
Pros and Cons of ESET PROTECT Enterprise
Like any solution, ESET PROTECT Enterprise has its strengths and weaknesses.
Pros:
- Comprehensive protection with multilayered technology
- Cloud-based management for ease of use and flexibility
- Advanced machine learning for accurate threat detection
- Full disk encryption for enhanced data security
Cons:
- The user interface may be complex for beginners
- Some users have reported slow customer support response times
Ideal Customer Profile for ESET PROTECT Enterprise
ESET PROTECT Enterprise is an ideal solution for medium to large businesses that require robust, comprehensive endpoint protection. Its advanced features and cloud-based management make it a suitable choice for organizations with a significant number of endpoint devices and a need for remote management capabilities.
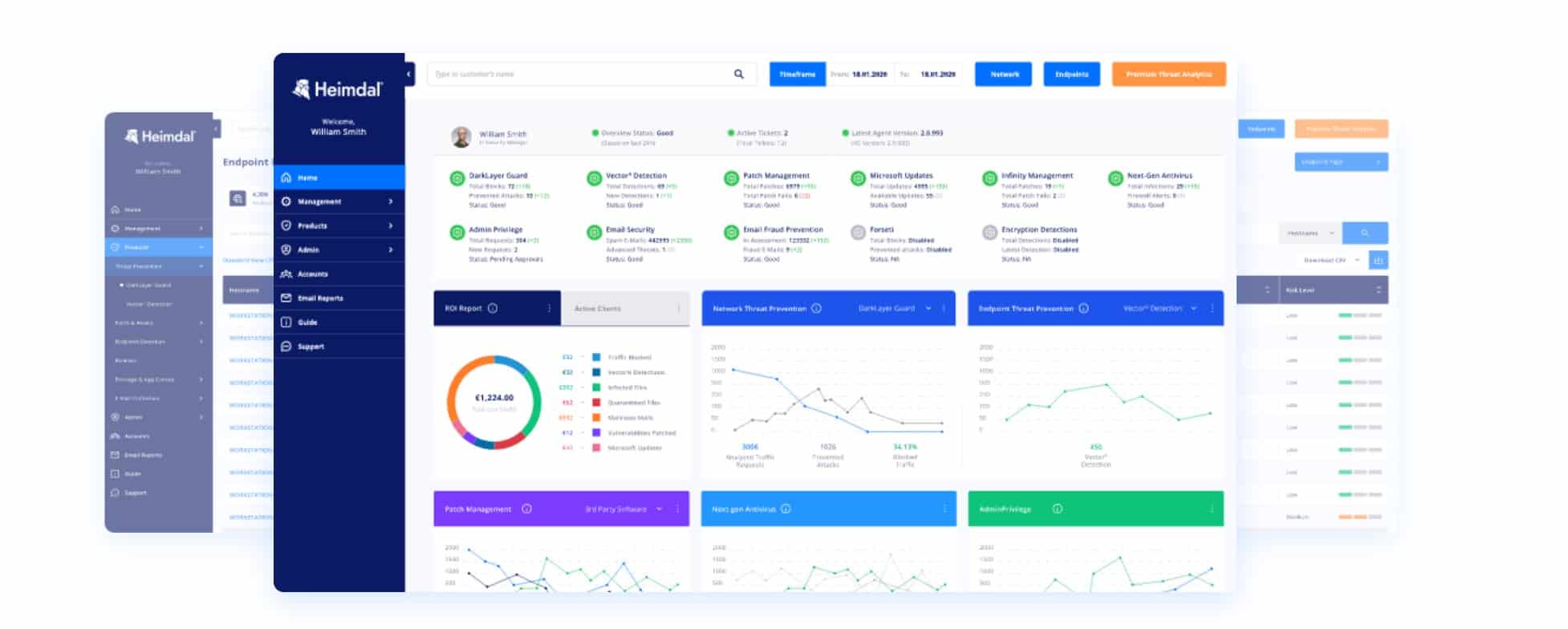
Heimdal™ Endpoint Detection and Response
Overview of Heimdal™ as a Provider
Heimdal™ Security is a fast-growing cybersecurity company that provides proactive security solutions beyond traditional antivirus measures. Founded in 2011 by the 2011 Defcon CTF World Champions in hacking, Heimdal™ Security has been on a mission to protect users against the most sophisticated cyber threats. With a strong emphasis on user education and a layered approach to security, Heimdal™ is a provider making waves in the cybersecurity industry.
Key Features of Heimdal™ EDR
Heimdal™ Endpoint Detection and Response (EDR) is a solution designed to provide organizations with a proactive approach to cybersecurity. Here are some of its key features:
- DarkLayer GUARD™: This unique tool analyzes network traffic to detect and mitigate threats before they reach your system.
- VectorN Detection™: This feature uses machine learning to detect and respond to advanced persistent threats and complex malware that may evade traditional antivirus solutions.
- Automatic Patch Management: Heimdal™ EDR automatically updates your software, eliminating vulnerabilities that cybercriminals could exploit.
- Incident Response and Forensics: This feature provides detailed reports on security incidents, allowing your IT team to analyze and respond effectively.
3. Pros and Cons of Heimdal™ EDR
Pros:
- A Proactive Approach to cybersecurity
- Unique features such as DarkLayer GUARD™ and VectorN Detection™
- Automatic patch management reduces the risk of software vulnerabilities
- Detailed incident response and forensics
Cons:
- Some users may find the range of features overwhelming
- The solution may be overkill for very small businesses
Ideal Customer Profile for Heimdal™ EDR
Heimdal™ EDR is an excellent solution for businesses of all sizes looking for a proactive approach to their cybersecurity. Its advanced features make it particularly suitable for organizations that handle sensitive data and require high protection. Thanks to its automatic patch management feature, it's also a great fit for businesses that lack the resources for regular manual patch management.

Cisco Secure Endpoint
Overview of Cisco as a Provider
Cisco Systems, Inc. is a multinational technology conglomerate headquartered in the heart of Silicon Valley in San Jose, California. Known for its networking hardware and software, Cisco has been a leader in the IT industry for decades. Over the years, Cisco has expanded its product portfolio to include a range of cybersecurity solutions, leveraging its vast experience and expertise to provide robust, reliable protection for businesses of all sizes.
Key Features of Cisco Secure Endpoint
Cisco Secure Endpoint, formerly AMP for Endpoints, is a comprehensive EDR solution that provides advanced protection against the most persistent and sophisticated threats. Here are some of its key features:
- Advanced Malware Protection: Cisco Secure Endpoint uses a combination of file reputation, machine learning, and continuous analysis to detect and block malware, including ransomware and file-less malware.
- Endpoint Isolation: In the event of a detected threat, Cisco Secure Endpoint can isolate the affected device to prevent the spread of malware.
- Threat Hunting: Cisco Secure Endpoint includes a threat hunting feature, which proactively searches for signs of malicious activity.
- Integrated Threat Response: This feature integrates with other Cisco products and third-party solutions for a coordinated response to threats.
3. Pros and Cons of Cisco Secure Endpoint
Pros:
- Comprehensive protection against advanced threats
- Endpoint isolation to prevent the spread of malware
- Proactive threat hunting
- Integration with other Cisco products and third-party solutions
Cons:
- Some users report that the user interface can be complex and difficult to navigate.
- The solution may be more expensive than other EDR solutions on the market.
4. Ideal Customer Profile for Cisco Secure Endpoint
Cisco Secure Endpoint is an ideal solution for medium to large businesses that require robust, comprehensive endpoint protection. It's advanced features and integration capabilities make it a suitable EDR system of choice for organizations with a significant number of endpoint devices and a complex IT infrastructure.
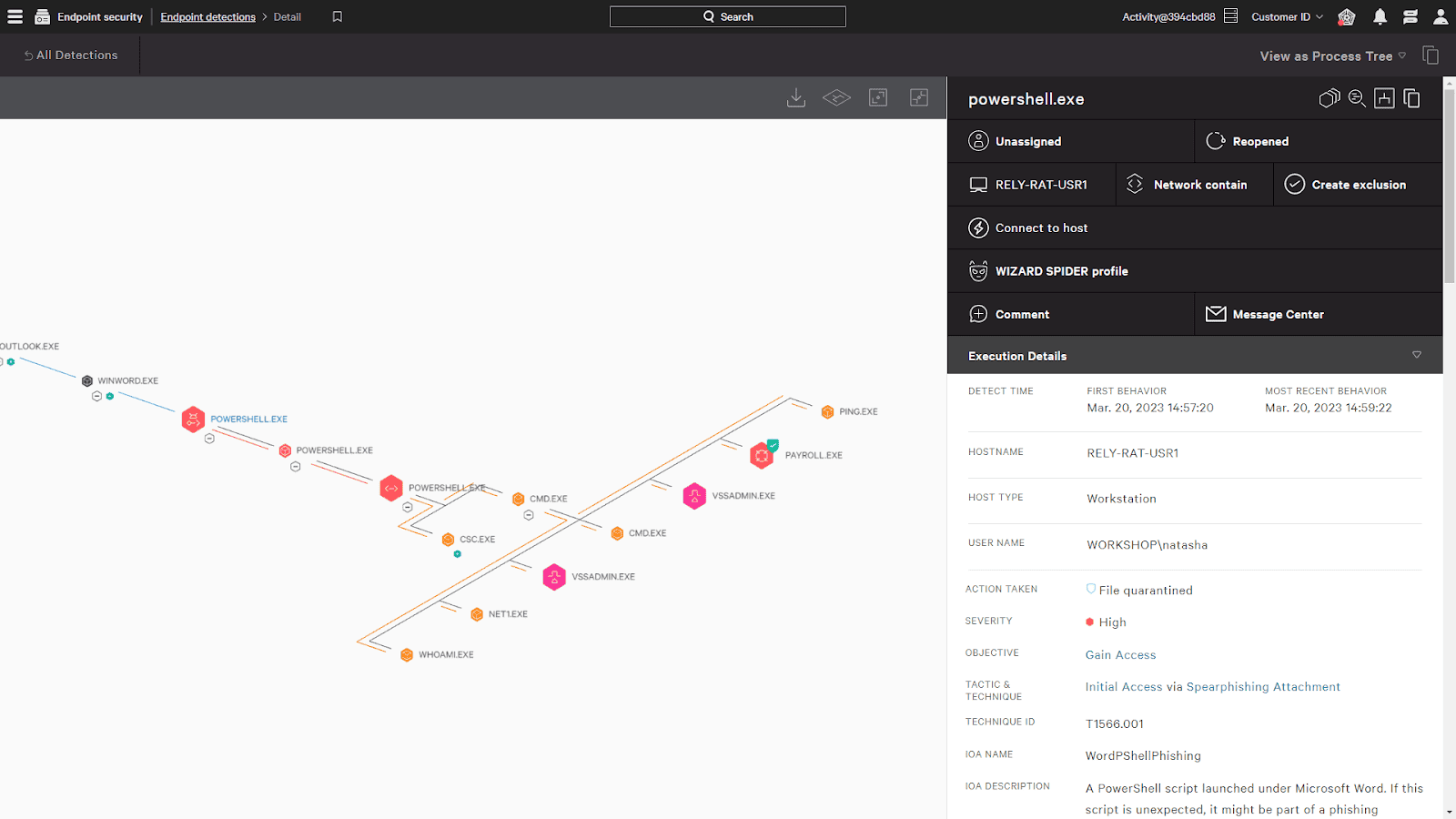
Falcon Insight by Crowdstrike
Overview of Crowdstrike as a Provider
CrowdStrike is a leading cybersecurity technology company that has revolutionized endpoint protection with its cloud-native approach. Founded in 2011, CrowdStrike has made a name for itself with its innovative solutions that stop breaches and protect businesses. With a focus on harnessing the power of artificial intelligence and cloud computing, CrowdStrike offers a range of products designed to provide superior protection against today's advanced threats.
Key Features of Falcon Insight
Falcon Insight is CrowdStrike's Endpoint Detection and Response (EDR) solution. It's designed to provide organizations with continuous, comprehensive visibility across all endpoints, helping to detect, prevent, and respond to threats in real-time. Here are some of its key features:
- Real-Time Response: Falcon Insight offers real-time response capabilities, allowing IT teams to respond to incidents as they occur.
- Threat Hunting: Falcon Insight includes a proactive threat-hunting feature, which uses sophisticated algorithms to detect signs of malicious activity.
- Cloud-Native Architecture: Falcon Insight leverages the power of the cloud to provide scalable, flexible, and reliable protection.
- Integrated Threat Intelligence: Falcon Insight integrates with CrowdStrike's threat intelligence to provide context and insights into threats.
Pros and Cons of Falcon Insight
Pros:
- Real-time response capabilities
- Proactive threat hunting
- Scalable, cloud-native architecture
- Integrated threat intelligence
Cons:
- Some users report that the solution can be complex to set up
- The cost may be prohibitive for smaller businesses
4. Ideal Customer Profile for Falcon Insight
Falcon Insight is an excellent solution for businesses of all sizes that require robust, real-time endpoint protection. Its cloud-native architecture makes it particularly suitable for organizations that need a scalable solution that can grow with their needs. Additionally, businesses that require integrated threat intelligence to inform their security strategies will find Falcon Insight valuable.
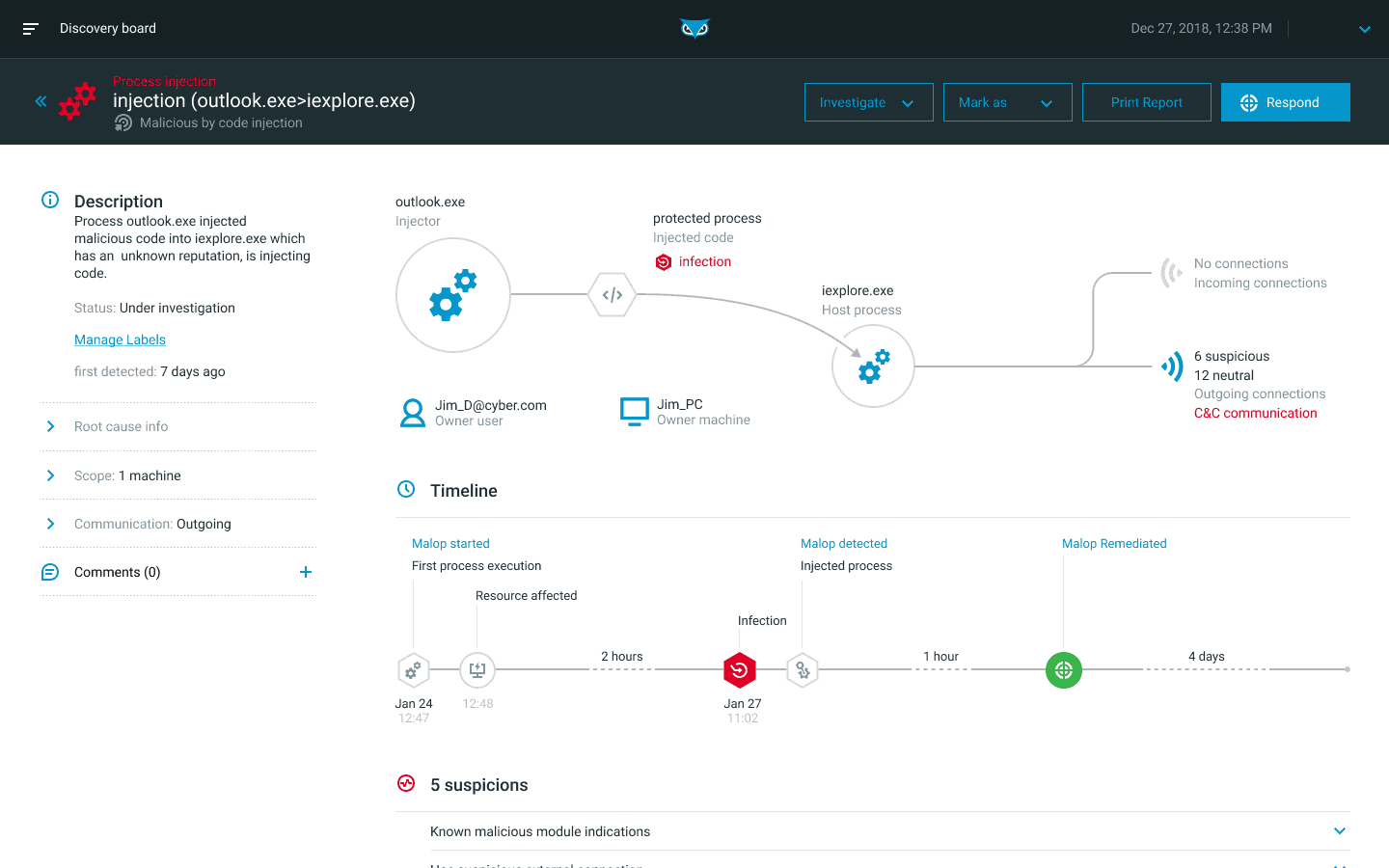
Cybereason Endpoint Detection And Response (EDR)
Overview of Cybereason as a Provider
Cybereason is a cybersecurity company dedicated to thwarting cyber attackers at every turn. Founded in 2012 by former members of military intelligence units, Cybereason has a deep understanding of how hackers think and operate, reflected in their innovative and comprehensive cybersecurity solutions. With a mission to protect enterprises against the most advanced cybersecurity threats, Cybereason provides a range of products designed to offer superior protection.
Key Features of Cybereason EDR
Cybereason Endpoint Detection and Response (EDR) is a solution designed to provide organizations with complete visibility across all endpoints, helping to detect, prevent, and respond to threats in real-time. Here are some of its key features:
- Malop Hunting: Cybereason EDR uses a unique approach called Malop (malicious operation) hunting, which focuses on detecting complex malicious operations rather than individual threats.
- Real-Time Response: Cybereason EDR offers real-time response capabilities, allowing IT teams to respond to incidents as they occur.
- Root-Cause Analysis: Cybereason EDR provides root-cause analysis for every Malop, giving IT teams the information they need to prevent future attacks.
- Threat Visualisation: Cybereason EDR includes a threat visualization feature, which visually represents the attack chain, making it easier to understand and respond to threats.
Pros and Cons of Cybereason EDR
Pros:
- Unique Malop hunting approach
- Real-time response capabilities
- Root-cause analysis for every Malop
- Threat visualization feature
Cons:
- Some users report that the user interface can be complex and difficult to navigate.
- The solution may be more expensive than other EDR solutions on the market
Ideal Customer Profile for Cybereason EDR
Cybereason EDR is an ideal solution for medium to large businesses that require robust, comprehensive endpoint protection. Its unique Malop hunting approach and root-cause analysis make it particularly suitable for organizations that want to understand and prevent complex malicious operations.
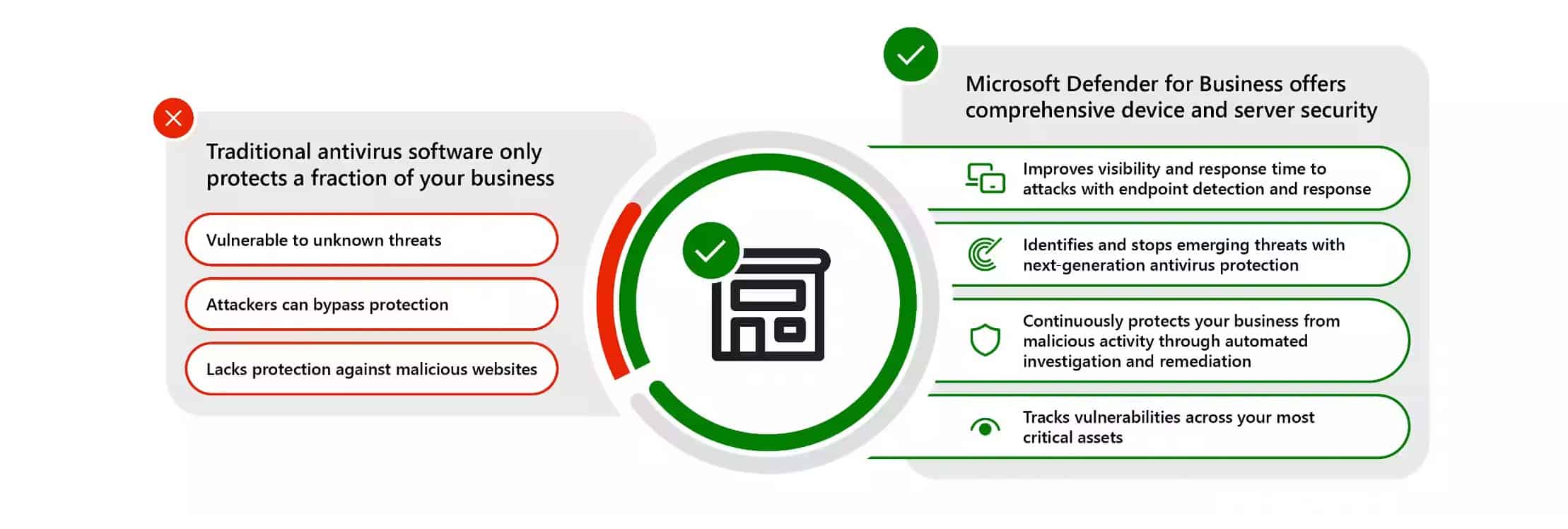
Bonus: Microsoft Defender for Endpoint
Overview of Microsoft as a Provider Microsoft is a multinational technology company that has been a leader in the industry for decades. Known for its software products like Windows and Office, Microsoft has also made significant strides in the cybersecurity space. One of their key offerings in this area is Microsoft Defender for Endpoint, a solution designed to secure endpoint devices across multiplatform enterprises.
Key Features of Microsoft Defender for Endpoint Microsoft Defender for Endpoint is a comprehensive endpoint security solution that offers a range of features designed to protect, detect, and respond to threats. Here are some of its key features:
-
- Holistic View: Microsoft Defender for Endpoint provides a holistic view of your environment, helping to eliminate blind spots by discovering unmanaged and unauthorized endpoints and network devices.
- Vulnerability and Misconfiguration Detection: The solution can discover vulnerabilities and misconfigurations in real-time, allowing quick remediation.
- Automated Alert Investigation and Remediation: Microsoft Defender for Endpoint can automatically investigate alerts and remediate complex threats in minutes, applying best practices and intelligent decision-making algorithms to identify active threats.
- Advanced Threat Detection and Response: The solution can detect and respond to advanced attacks with deep threat monitoring and analysis.
- Mobile Device Security: Microsoft Defender for Endpoint also offers features to secure your mobile devices.
Pros and Cons of Microsoft Defender for Endpoint Pros:
-
- A comprehensive endpoint security solution
- Real-time detection of vulnerabilities and misconfigurations
- Automated investigation and remediation of alerts
- Advanced threat detection and response capabilities
- Mobile device security
Cons:
- As with any solution, there may be a learning curve for users unfamiliar with the platform.
- Some users may find the range of features overwhelming.
Ideal Customer Profile for Microsoft Defender for Endpoint Microsoft Defender for Endpoint is suitable for businesses of all sizes, particularly those that operate in a multiplatform environment. Its comprehensive feature set makes it an ideal solution for organizations seeking robust endpoint protection that can discover, prioritize, and remediate vulnerabilities and threats.
Future of Endpoint Detection and Response Tools
As we navigate the ever-evolving landscape of cybersecurity, it's clear that Endpoint Detection and Response (EDR) solutions will continue to play a pivotal role in safeguarding our digital assets. But what does the future hold for Endpoint Solutions? Let's explore some emerging trends and how they could shape the future of EDR.
Emerging EDR Features
- Integration with Other Security Tools: As cybersecurity threats become more complex, there's a growing need for integrated security solutions. We expect to see more EDR solutions offering seamless integration with other security tools, providing a more holistic approach to cybersecurity.
- AI and Machine Learning: Artificial Intelligence (AI) and Machine Learning (ML) have already made significant inroads into EDR solutions, and this trend is set to continue. These technologies enable EDR solutions to detect and respond to threats more quickly and accurately, and their role will only become more critical as cyber threats continue to evolve.
- Increased Focus on Threat Hunting: Proactive threat hunting is becoming a key feature of EDR solutions. This involves actively searching for signs of malicious activity within an organization's network rather than waiting for an alert to trigger an investigation.
- Cloud-Based EDR: As more organizations move their operations to the cloud, we expect a corresponding increase in cloud-based EDR solutions. These offer a range of benefits, including scalability, cost-effectiveness, and the ability to monitor and protect remote workers.
How These Trends Could Shape the Future of EDR
These emerging trends are set to shape the future of EDR in several ways.
Integrating EDR platforms with other security tools will lead to more comprehensive and effective cybersecurity strategies. Organizations will be able to respond to threats more quickly and efficiently, reducing the potential impact of cyber-attacks.
Secondly, the continued advancement of AI and ML in EDR solutions will lead to more accurate threat detection and response. This will be particularly important in combating advanced persistent threats, which can evade traditional security measures.
Thirdly, the increased focus on threat hunting will enable organizations to detect threats earlier in the attack lifecycle, potentially preventing breaches before they occur.
Finally, the rise of cloud-based EDR will provide organizations with more flexible and scalable solutions, making protecting an increasingly distributed workforce easier.
Conclusion
As we wrap up our exploration of the top 5 Endpoint Detection and Response (EDR) solutions, it's clear that EDR is essential to any robust cybersecurity strategy. From ESET PROTECT Enterprise's comprehensive protection to Cybereason's unique Malop hunting approach, each solution offers unique features that can help safeguard your organization's digital assets.
Choosing the right EDR solution for your organization is a critical decision. It's important to consider not only the features of the solution but also its compatibility with your existing infrastructure, the needs of your IT team, and the specific threats your organization faces.
Remember, the best endpoint solution is one that provides comprehensive visibility across all endpoints, detects threats in real-time, and has effective response features to mitigate any potential damage. It should also be scalable to grow with your organization and flexible enough to adapt to evolving cyber threats.
As we look to the future, we can expect EDR solutions to become even more sophisticated and integral to our cybersecurity strategies. With the continued advancement of technologies like AI and machine learning and the growing focus on proactive threat hunting and integrated security, the future of EDR is indeed promising.
In the face of ever-evolving cyber threats, investing in a robust EDR solution is not just a smart move—it's a necessity. So, take the time to explore these top 5 EDR solutions and choose the one that best fits your organization's needs. After all, in cybersecurity, the best defense is a strong offense.
FAQ
Q: What is EDR? EDR stands for “Endpoint Detection and Response.” It is a cybersecurity solution that monitors and detects endpoint activities and provides automated responses to potential threats.
Q: What are the benefits of using an EDR tool? The benefits of using an EDR tool include increased endpoint security, improved endpoint protection, extended detection and response, and faster response to potential threats.
Q: What are the features of EDR tools? EDR tools provide endpoint visibility, endpoint threat detection, automated response, investigation and response capabilities, and full EDR capabilities for endpoint security.
Q: What is XDR? XDR stands for “Extended Detection and Response.” It is a more comprehensive cybersecurity solution than EDR that not only monitors endpoint activities but also includes monitoring for network and cloud activities.
Q: How does EDR differ from an Endpoint Protection Platform? While Endpoint Protection Platforms focus on preventing known malware and attacks, EDR solutions monitor endpoint activities and provide response capabilities to unknown or potential threats.
Q: How do EDR tools provide automated responses? EDR tools use an agent installed on endpoint devices to monitor activities and detect potential threats. When a threat is detected, the EDR solution can automatically respond or provide recommended actions for security personnel.
Q: What is the best EDR solution for my security team? The best EDR solution for your security team depends on your organization’s needs and priorities. It is recommended to review and compare the features of EDR tools and evaluate their effectiveness and capabilities.
Q: How do EDR solutions monitor endpoints? EDR solutions monitor endpoints by collecting data from the agent installed on endpoint devices and analyzing the data for potential threats or abnormal activities.
Q: How can EDR solutions help with endpoint management? EDR solutions provide endpoint visibility and monitoring capabilities to help manage endpoints. They can detect and troubleshoot endpoint issues and provide valuable insights for improving endpoint security.


